Getting The Data Security Services To Work
Table of ContentsAbout Data Security ServicesThe Of Data Security ServicesThe Single Strategy To Use For Data Security ServicesFacts About Data Security Services RevealedData Security Services for Dummies
Reliable information safety employs a collection of controls, applications, and approaches that establish the value of various datasets and use the most ideal safety and security controls. Data safety and security that works consists of the level of sensitivity of varied datasets along with regulatory compliance requirements. Information safety and security, like various other cyber safety postures such as border and documents safety, isn't the all-important element for keeping cyberpunks away.
Because of this, information safety stays one of the most crucial concerns for any kind of major organization. Since the scope of how to take care of information security is so wide, a solitary method will certainly not have the ability to close all possible defects. Because of this, we use a variety of strategies to manage this issue.
Data erasure ensures that information can not be recovered and so will not come under the incorrect hands. Organizations can enable teams to create applications or train individuals using real information by covering up data. It conceals directly identifiable info (PII) where needed to enable growth to happen in certified contexts.
The Single Strategy To Use For Data Security Services
It was constantly possible that it would certainly can be found in useful at some time in the future. From a safety and security element, large quantities of data are now taken into consideration an obligation. The even more information you have, the more prospective targets you have for hackers. As an outcome, data reduction has actually become a critical safety and security approach.
Whether we're speaking concerning bank consumer information or healthcare facility individual information, this is delicate information that shouldn't be shared with simply any individual. All of this information is kept safe as well as safe and secure through information protection.
Whether your data is kept on-premises, in a company data centre, or in the general public cloud, you must confirm that the centers are secure which sufficient fire suppression as well as climate controls are in location. These protection precautions will certainly be taken care of by a cloud provider on your behalf.
With the quantity of information being developed and also stored daily, information defense is coming to be more and much more critical. Firms release approaches that permit information to be brought back after any type of corruption or loss.
Data Security Services Things To Know Before You Get This
As an example, not all information in a firm has actually to be seen by all the employees. Personal information have to remain private between the worker and the human resources department. Keeping that said, data defense can help in maintaining such data from prying eyes. Keeping your information safeguarded additionally assists you stay ahead of your rivals.
In several industries, information security is a must, as well as your software program needs to have stringent protection procedures to satisfy present go to my site needs. Some of the key information safety criteria to adhere to are: The Repayment Card Industry Information Protection Criterion is a significant safety criterion for any kind of services handling settlement card info.
For services that have their site, a potential cyber violation could create a significant issue. If your data is accessed by unapproved individuals, it's feasible that your web site discover this might be required to shut or you may experience downtime. This could influence your income as you will certainly shed money from shed transactions.
Outsourcing a trusted managed IT solutions carrier will permit you to manage the specific demands of your service. In this manner, you can assure that you will obtain the best quality of IT solutions as well as all your information are always kept secure.
Data Security Services for Dummies
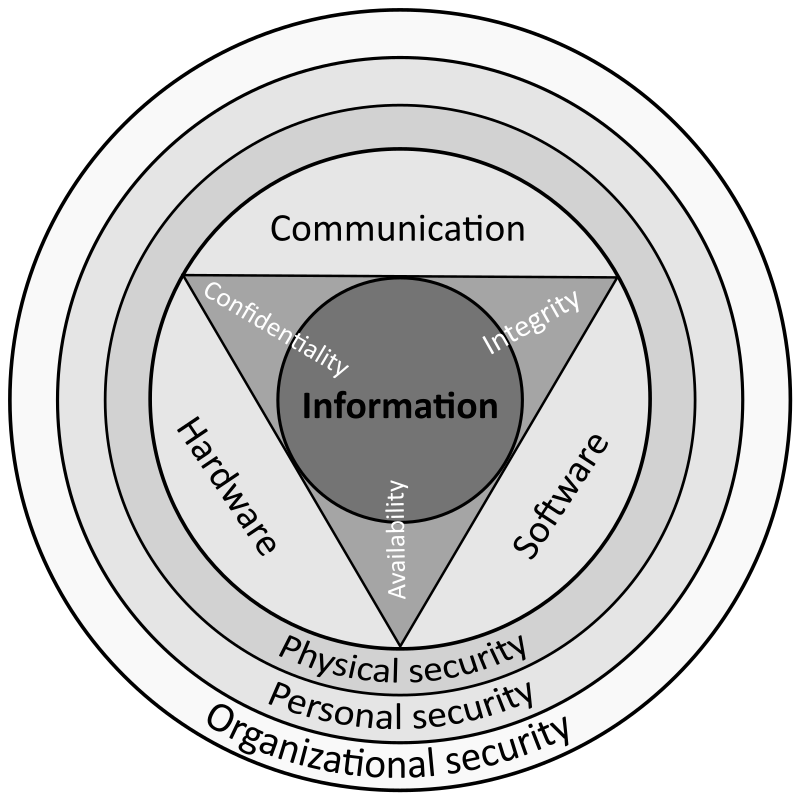
It's the factor data security is fairly beneficial. Data safety keeps all this details precisely where it's meant try this website to be.
They can also introduce a very harmful virus which contaminates the entire system, such as ransomware, calling for the repayment of a ransom charge in order to regain accessibility to your networks and also delicate information. Poor information safety and security could bring about an event which adversely impacts your company. Also the capability to conduct normal company may be altered.
: All data, whether the human resources data source, electronic spreadsheets, or accounts files, ought to be supported. data security services. In case of equipment or software failure, violation, or any various other error to data; a back-up enables business to continue with marginal disturbance. Storing the files elsewhere can also swiftly determine exactly how much information was shed and/or corrupted.
The 6-Minute Rule for Data Security Services
In instance of unintended information loss, you have a fallback plan. It does not matter how large or tiny your organization is, you require to prioritize data security.